Load balancers
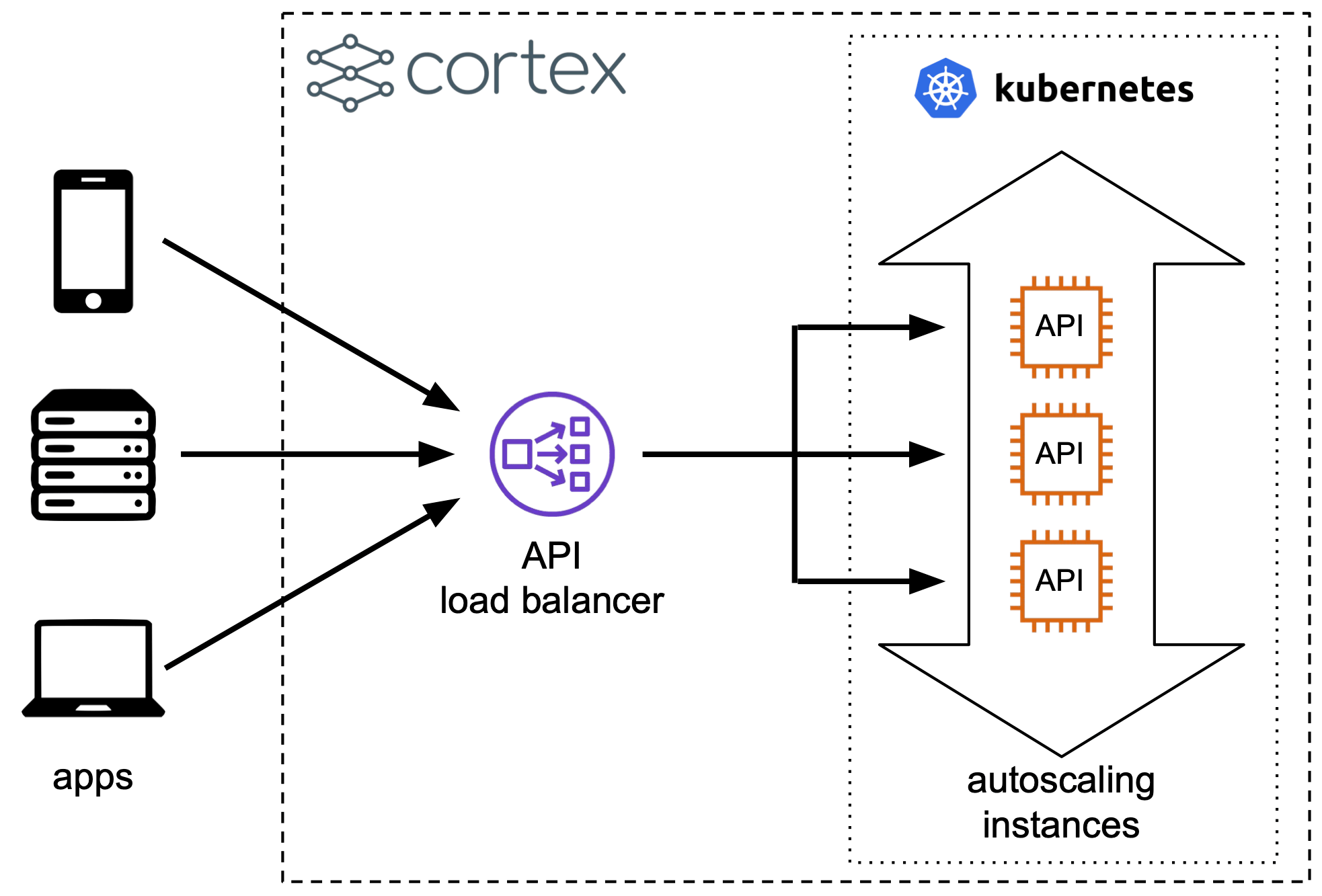
All APIs share a single API load balancer. By default, the API load balancer is public. You can configure your API load balancer to be private by setting api_load_balancer_scheme: internal in your cluster configuration file (before creating your cluster). This will make your API only accessible through VPC Peering. You can enforce that incoming requests to APIs must originate from specific ip address ranges by specifying api_load_balancer_cidr_white_list: [<CIDR list>] in your cluster configuration.
The SSL certificate on the API load balancer is autogenerated during installation using localhost as the Common Name (CN). Therefore, clients will need to skip certificate verification when making HTTPS requests to your APIs (e.g. curl -k https://***), or make HTTP requests instead (e.g. curl http://***). Alternatively, you can enable HTTPS by using a custom domain and setting up https or by creating an API Gateway to forward requests to your API load balancer.
There is a separate load balancer for the Cortex operator. By default, the operator load balancer is public. You can configure your operator load balancer to be private by setting operator_load_balancer_scheme: internal in your cluster configuration file (before creating your cluster). You can use VPC Peering to enable your Cortex CLI to connect to your cluster operator from another VPC. You can enforce that incoming requests to the Cortex operator must originate from specific ip address ranges by specifying operator_load_balancer_cidr_white_list: [<CIDR list>] in your cluster configuration.
By default, the API load balancer and Operator load balancer are both Network load balancers (NLB). The api load balancer can be configured as a Classic load balancer (ELB) instead if desired. The API load balancer type must be specified before creating your cluster.
Last updated